Breached in March, Leaking Now
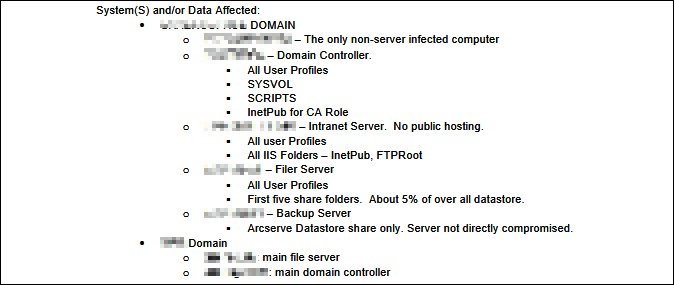
Maze ransomware is one of those few groups that target only institutions rather than individuals, and also popularized the concept of leaking the stolen data, which would pressure the victim into paying the ransom. The group has written in its leak site that, it had breached the ST Engineering’s network back in March this year, and has stolen unencrypted files and encrypted systems of AT San Antonio Aerospace corp, a wing of ST Engineering. Supporting their claims, they’ve also posted 100 documents related to AT SAA’s financials, expired NDAs, proposals and cyber insurance contracts. These also reveal its links Chubb, which was also attacked by Maze group in March this year. Further, reports also show that ST Engineering is aiding political parties in Latin America and CIS. While it’s not revealed how the group has infected AT SAA’s network, a memo from its IT manager explains everything. The IT manager’s cyberattack memo reveals that Maze has first connected to AT SAA’s servers via RDP, through a comprised admin account. This allowed them to comprise the default domain admin account and takeover the company’s domain controllers, intranet servers, and file servers on two domains. It also states the companies have recovered the infected systems within three days of being hit from Maze ransomware. And since the data is huge and sensitive, AT SAA is subjected to inform its customers. And it’s unclear how much the ransom is being demanded. AT SAA’s General Manager and Vice President, Ed Onwe said they had limited the attack by disconnecting some of their critical systems in time and will be investigating the issue to know more. Via: BleepingComputer