A New Modular Malware in Wild
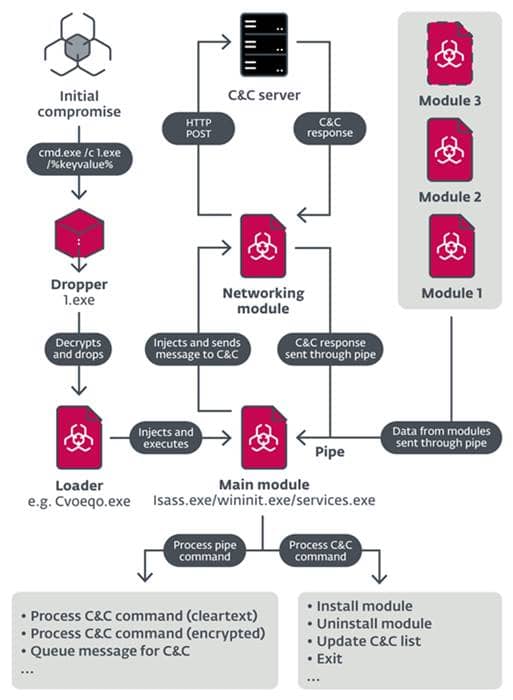
As per a report from ESET, a new modular malware named ModPipe targets the Oracle PoS systems. More specifically, it’s hitting Oracle’s Micros RES 3700 models widely used by the companies in the hospitality industry. This malware is one of a kind since having several modules, which lets it to add more features by downloadable components. While researchers have found some basic components in late 2019, they have listed three downloadable modules used by ModPipe to process its job. These are; GetMicInfo – for stealing the database passwords and various other data. ModScan – for running scans on IP addresses that are defined by the hacker. ProcList – to list out all the running processes and their modules. Besides these three, researchers say there could be four more modules which are yet to be documented. While it’s still unknown how this malware is compromising the PoS systems, the mechanism of what it goes through is described. Suppose said to have a dropper initially, a persistent loader, the main module, a networking module, and downloadable components. Talking in detail about the three known components, GetMicInfo is a password stealer that exploits the decrypting from the Windows Registry key. Unfortunately, the decryption mechanism of GetMicInfo, too, is yet to be explained. Though it steals the password for accessing the database, researchers say the data could still be safe. The sensitive details like the card’s number and CVV code are encrypted and require the hacker to know the paraphrase and set that into their malware to crack and retrieve. This happened anyway, hinting the hacker may have reverse-engineered PoS systems’ workings to learn how they’re encrypted and decrypted, or setting another module to decrypt the password or buy it in the underground forum, which could have been gathered from an earlier hack. While there’s a lot to learn about this first component yet, the next one in the row, ModScan, is meant for gathering data about the PoS environment by scanning IP addresses that are being defined. These could be the version number of Oracle Micros RES 3700, the database’s name, and the database server data. Finally, ProcList is designated for procuring details about the processes currently running in the targeted system. These could be like the process identifier (PID), parent process PID, number of threads, token owner, token domain, process creation time, and command line.
New Hacker Group Actively Exploiting Zero-Day Bug in Oracle Solaris OS ByteDance Drops Microsoft and Picks Oracle as TikTok Owner in the US Ragnar Locker Ransomware Uses Oracle VirtualBox to Steal Data Stealthily