Banking on the Biggest Movement
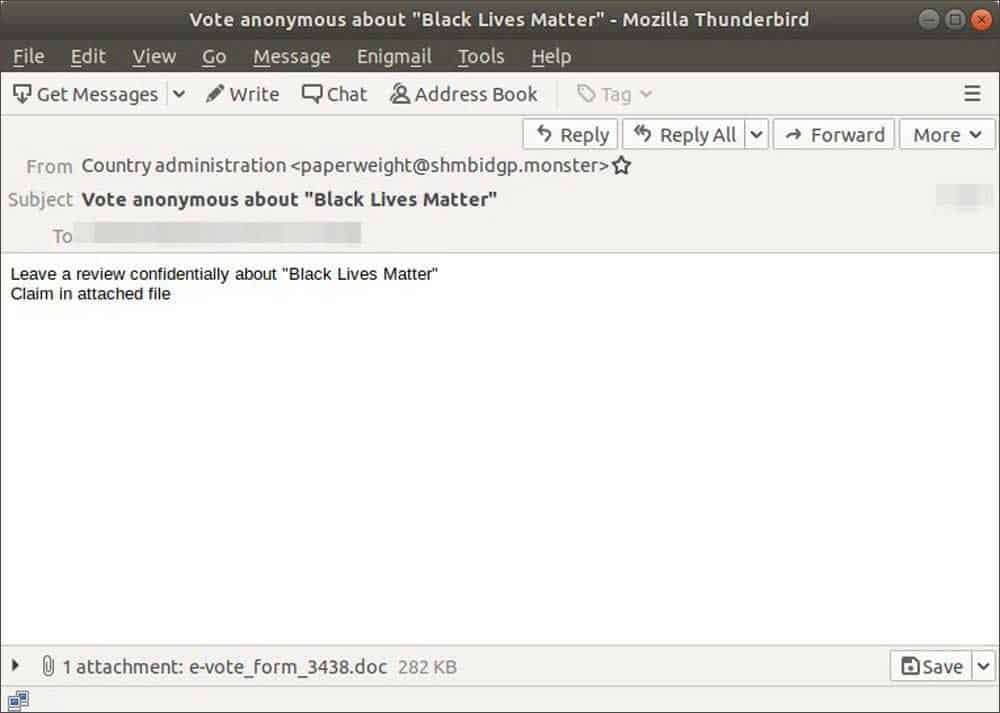
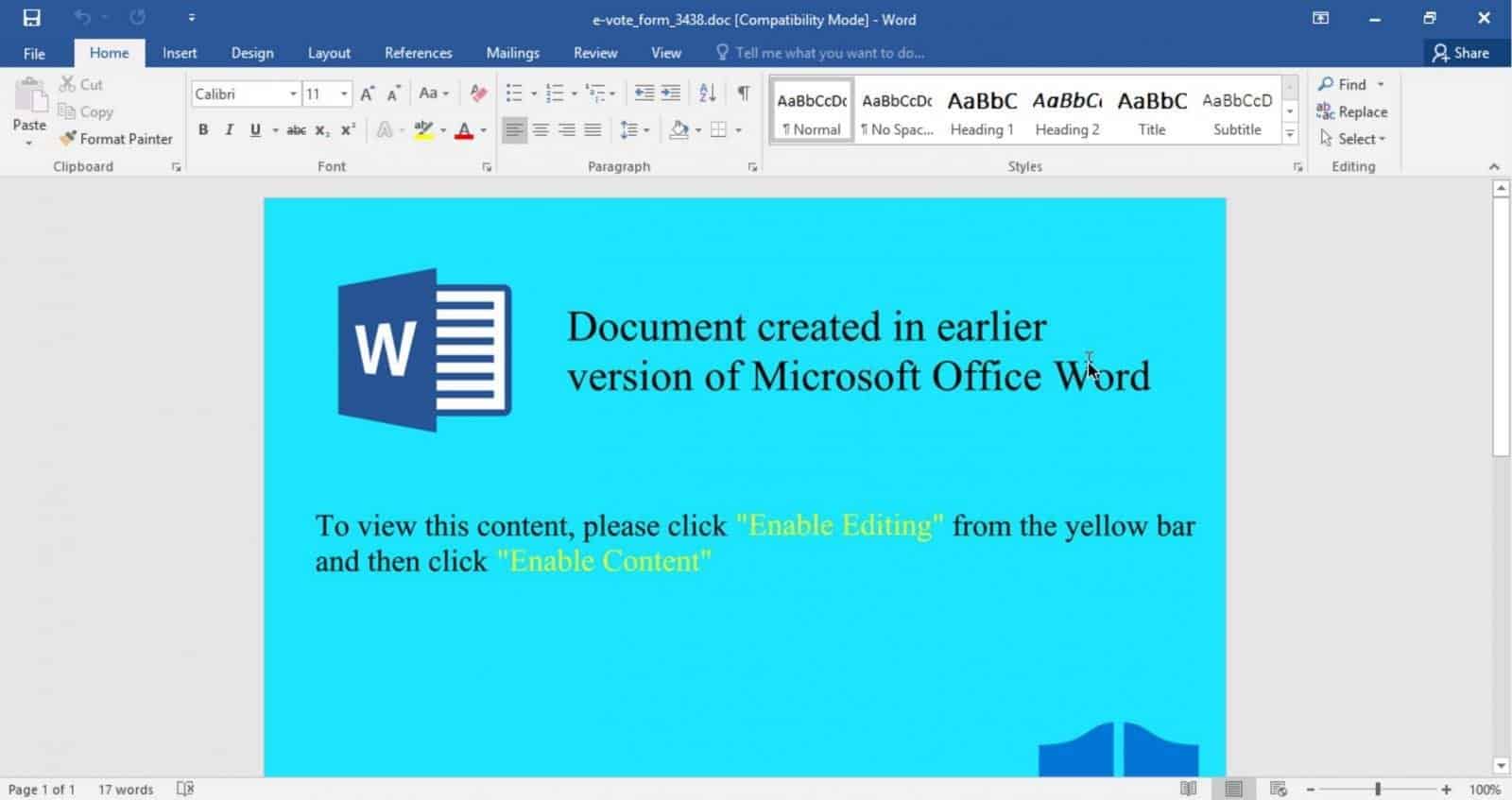
Trickbot malware has grown its name as a banking trojan in the past. And it’s now developed with various features to not just steal banking details, but also other login credentials, spreading across networks and even setting backdoors to dump other payloads. It’s even reported that Trickbot has partnered with ransomware operators to let them access through Trickbot’s backdoors! While all these are worrying, here’s a new reason to worry more. The authors of Trickbot malware now seem to be banking on the active movement of Black Lives Matter. As BleepingComputer reported, there’s an active phishing campaign by adversaries disguised as Country’s administration, and asking users to vote anonymously on the Black Lives Matter movement. The email content directs to a Word document attachment that has a file to be answered and sent back, titled as e-vote_form_3438.doc. And when opened, the document prompts to Enable Editing or Enable Content to view the contents properly. This, if enabled, the document will allow Trickbot malware in the form of a DLL file and executes it on the device. And since it’s featured with many powers, the malware steals sensitive information and spread across the network through connected devices. Phishing attacks of such have increased during this pandemic led lockdown, as most of the population is restricted to home and replying much on unsecured technology, it’s a good opportunity for hackers to bank upon them. Experts have long been warning users not to open suspicious emails or attachments, and look regularly for any malicious softwares on their devices. Via: BleepingComputer